
Did you know there are 5,000 new Android apps that can harm your device or steal your data – including extreme cases, such as a Russian fake version of Google Play that would add charges to your mobile bill? Those nuggets are included in the latest quarterly security roundup from Trend Micro’s Labs. The report, released last week, breaks little new ground but makes information on the latest threats accessible in a very concise and attractive format.
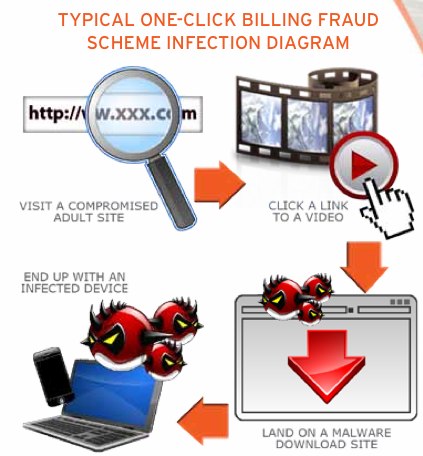
Another scheme in Japan resulted in the police there arresting six individuals involving a one-click billing scheme. Typically, as shown in the diagram to the right, a user would visit a compromised site, click on a link to play a video, and end up with an infected device. The Japanese scheme netted some $150,000.
Another nasty piece of business is what is called “Ransomware,” which is a set of malware that infects a user’s machine and holds his or her files hostage. Sometimes, the software will encrypt part of your hard drive, demanding money before allowing you to decrypt the files. In one case, users saw a splash screen that demanded they pay a 100 euro fine for viewing porn or other questionable material on the computer.
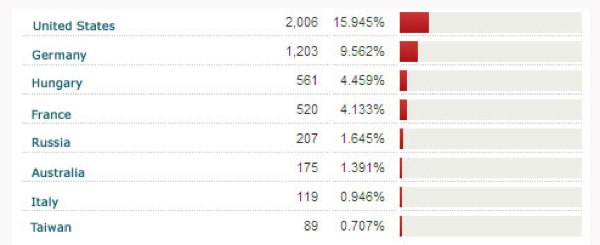
Ransomware is now branching out to other countries in Europe, and has a big footprint in the U.S., as you can see here:
Part of the problem is that installing a mobile app is so easy, many users do it almost unconsciously, so it often doesn’t get the same kind of due diligence that desktop applications get. Combined with the willingness of many Gen Yers to share personal information, and it’s easier than ever for the bad guys to spread malware and steal your data, your money, or both.
As part of its security scanning efforts, TrendLabs processes more than four terabytes of data each day and analyzes some 8 billion URLs and 200,000 IP addresses. The report also includes the company’s top 10 blocked URLs or malicious domains.
It is well worth a closer read.
Read more : 5,000 Dangerous Android Apps Says Trend Micro Report

0 Responses
Stay in touch with the conversation, subscribe to the RSS feed for comments on this post.